Integrated Cybersecurity Program

Strong Cybersecurity and Compliance is a "License to Operate"
Is the key to winning trust and closing deals with prospects.
SLAs play a significant role in supporting trust as well. RegSec solutions must work with existing technology and be financially viable.
Without a continuous integrated approach, your cybersecurity and compliance program will not be sustainable.
Regulators increase pressure on companies to implement safeguards to protect customer’s information and own data.
Over the past year, the legal Duty of Care concept in cybersecurity was broadened. Multiple privacy laws and cybersecure industry laws such as HIPAA and LGBA.
Legal Requirements
Duty of Care is a legal obligation imposed on an organization, requiring adherence to a standard of reasonable care while preventing any acts that could foreseeably harm others.
Legal Requirements
Duty of Care is a legal obligation imposed on an organization, requiring adherence to a standard of reasonable care while preventing any acts that could foreseeably harm others.

Main Challenges

Main Challenges
Build a cybersecurity program to avoid, lower, or outsource operation risks including service disruptions, fines lawsuits, and reputation damage.
Empower sales organization with a documented cybersecurity management framework that would enable them to sell with less friction.
Simplify the burden of Cybersecurity Due Diligence questionnaires and weight of client’s requirements for cybersecurity management, allowing cost optimization.
Assure to comply with new client’s requirements for cybersecurity management and legal regulations. Be adaptive to new requirements, regulations, and changes to technology footprints and business structures.
What you get
Build a safe digital environment with professionals for whom your data and privacy are always a top priority








Values We Guarantee:
30% faster to respond
to client’s RFPs and Cybersecurity Due Diligence Questionnaires, reducing time and cost while increasing sales revenue.
95% alignment
of cloud IT to compliance requirements during first 90 days.
70% reduction
of executive involvement 30% reduction of staff involvement.
60% more efficient
in adopting new compliance regulations.
90% increase
of operational ability during incidents and CIRT work.
What Do You Get From Digital Edge?
Build a safe digital environment with professionals with whom your data and privacy are always a top priority

How we work:
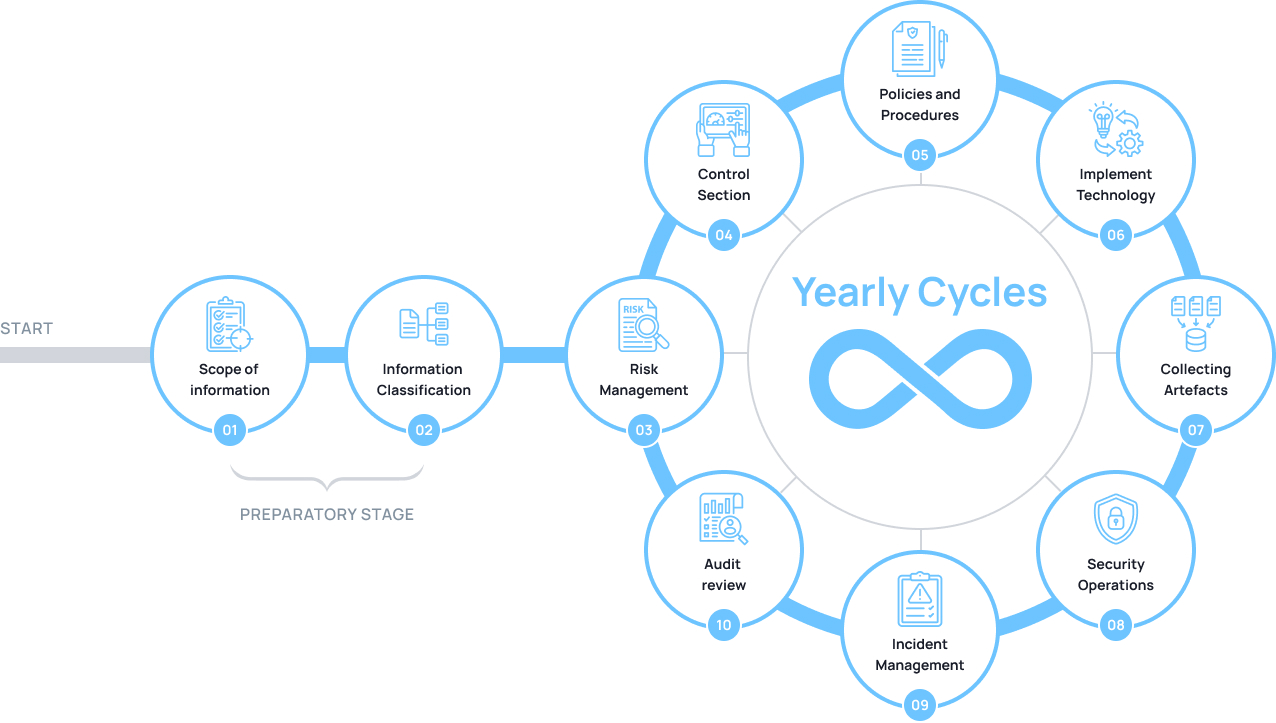
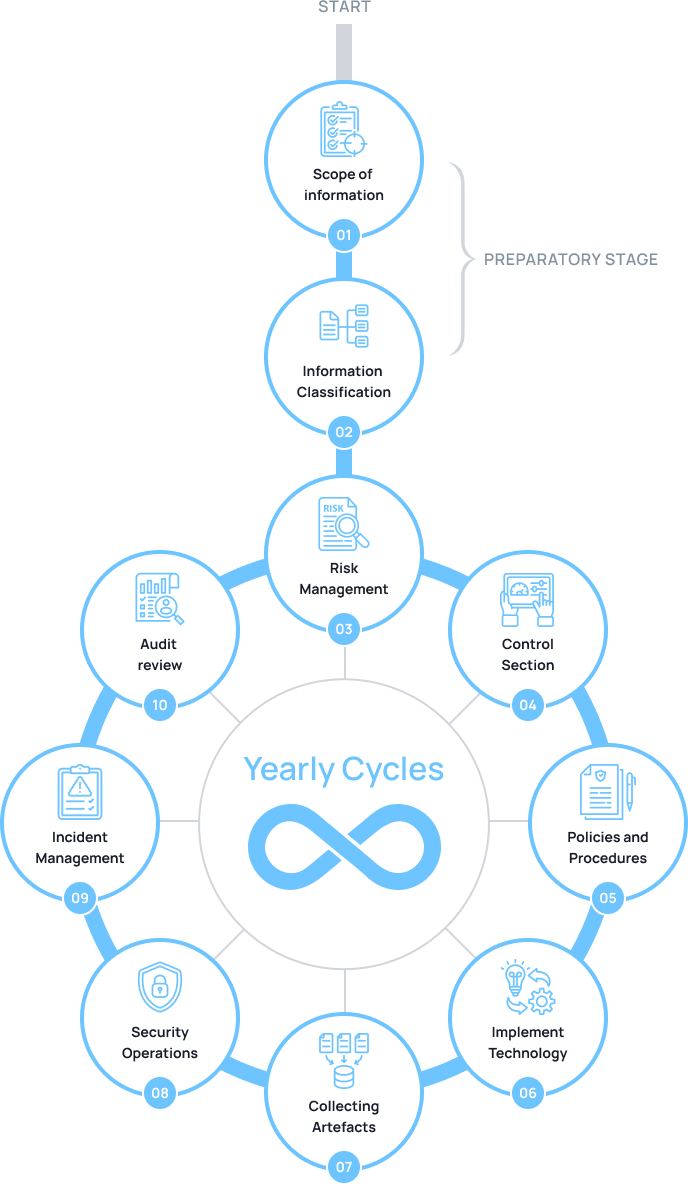
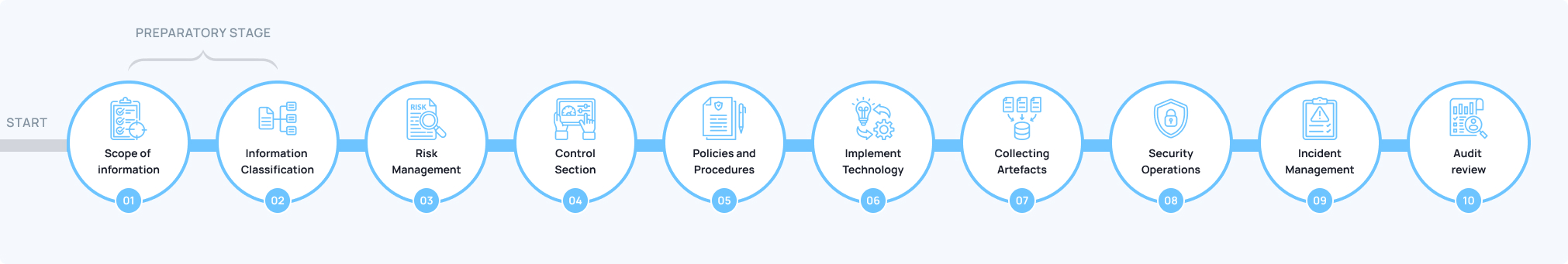
Ready to protect your organization?
Our IT experts are ready to help you identify vulnerabilities and opportunities to strengthen your cybersecurity defenses.
Ready to protect your organization?
Our IT experts are ready to help you identify vulnerabilities and opportunities to strengthen your cybersecurity defenses.


